MS Windows
Microsoft Windows is a desktop and server operating system (software). Various services and programs that run Windows produce log events. These log events are maintained at the system level, by event log category and source program.
The LogZilla Windows Syslog Agent is a Windows service, developed and provided by LogZilla Corp, that reads these Windows log events from the system that the Agent service is running on. Then the Agent conveys these log events to the LogZilla server for recording and processing. For the Agent, version 2.0.0.0 or greater is required. It is highly recommended to use the most recent version, available on the LogZilla "extras" github.
App Function
NOTE: Although the LogZilla Windows Syslog Agent conveys all the data elements that Windows indicates are associated with a given event, by default the MS Windows appstore app does not process or otherwise use these additional data elements. There are too many possible data elements with differing values to store these elements and values by default.
There may well be important uses for these additional data elements so in many cases it will be worthwhile to create an additional custom app or rule that provides processing subsequent to the main appstore app execution, that then converts these additional data elements to user tags or performs other handling. If you are unfamiliar with how to accomplish this, contact LogZilla support to receive assistance.
Vendor Documentation
Incoming Log Format
The Windows "native" event log format is shown in the next section. However with regards to LogZilla usage, Windows events are converted into a JSON data element that lays out the important data associated with that event. An example of this is also given below.
Example Logs
This shows the raw log message text for a typical logged event:
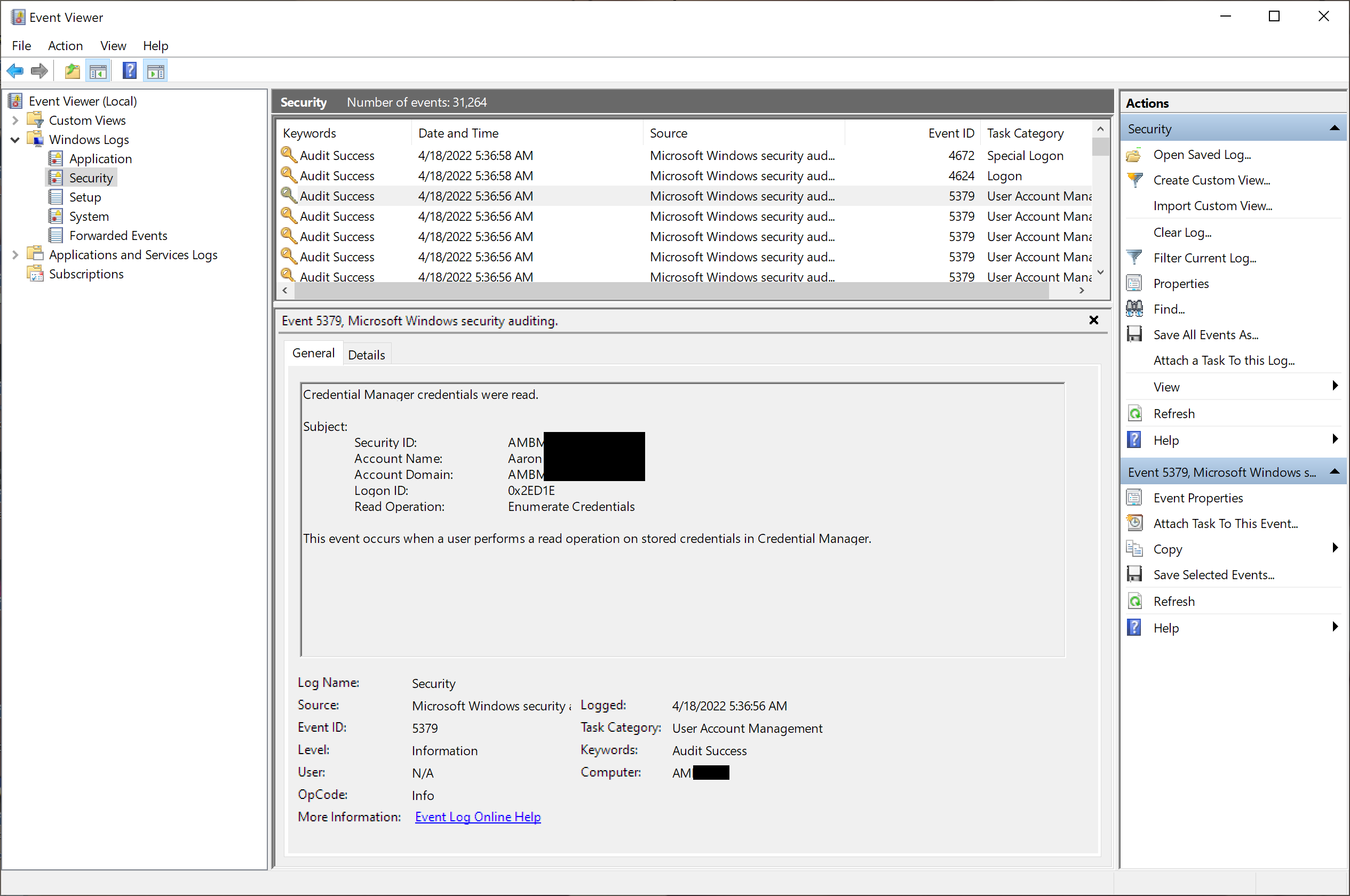
This shows the raw data elements associated with that logged event:
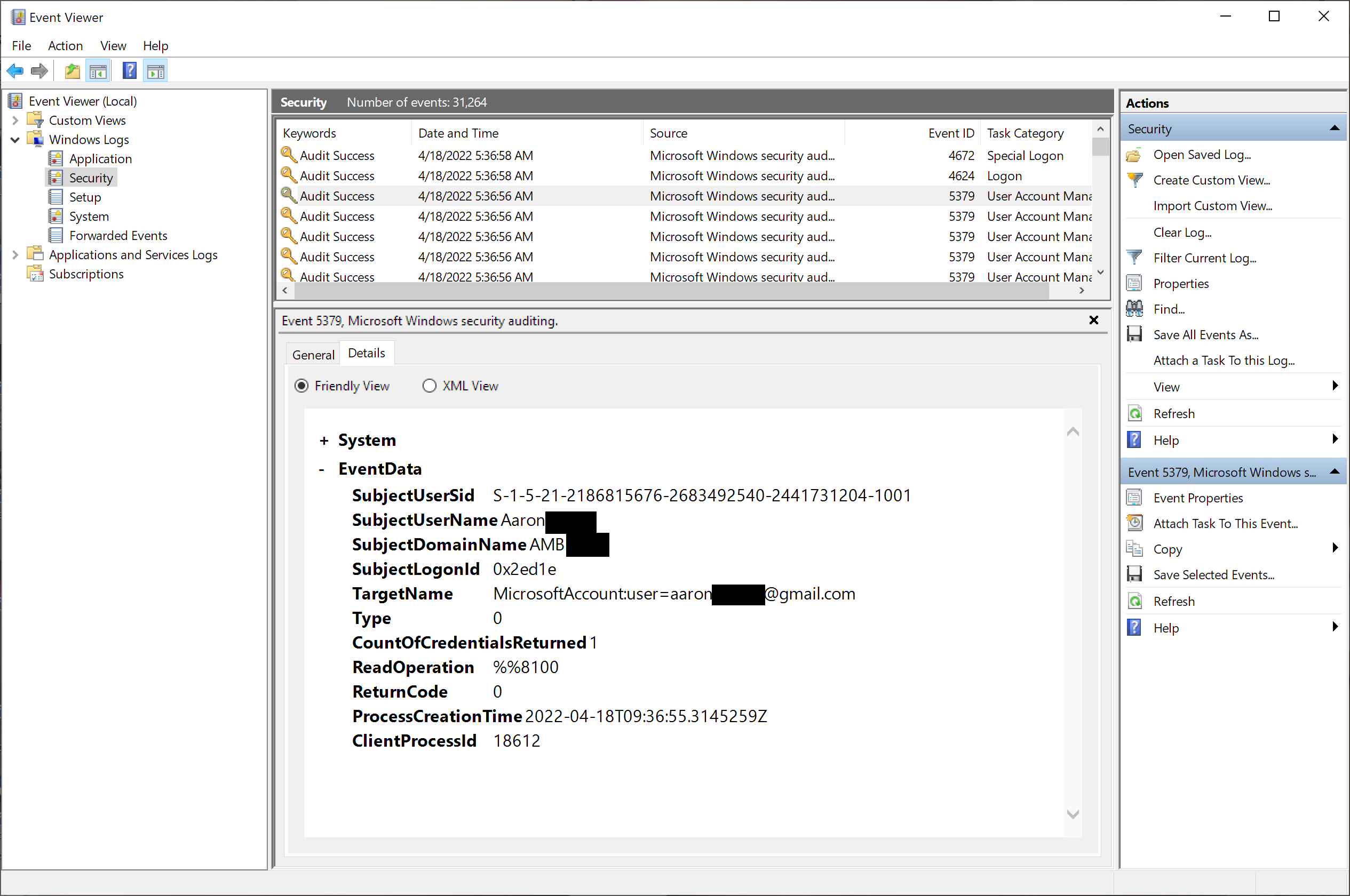
This shows a raw XML view of those same data elements associated
with that logged event:
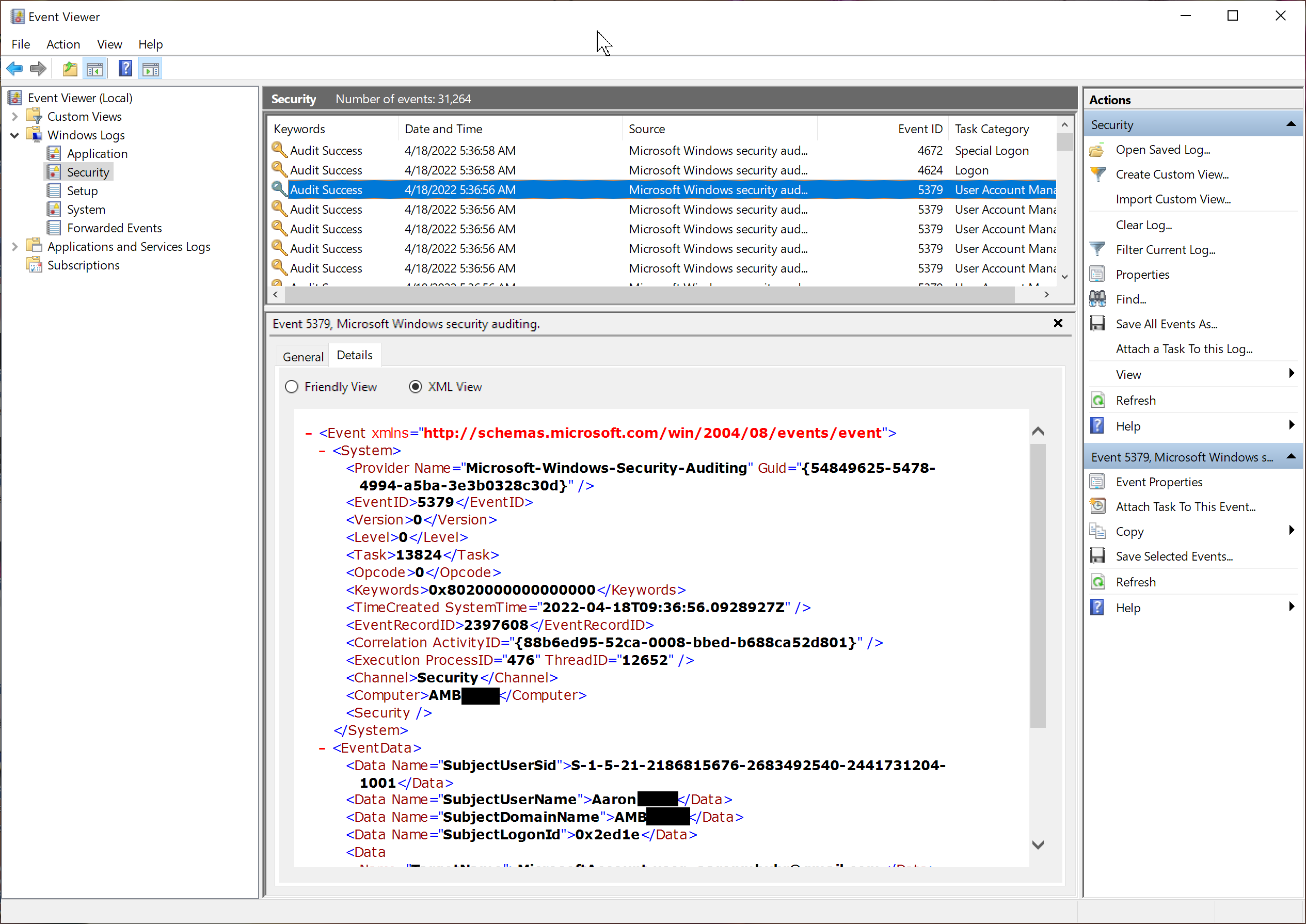
This is an example of the JSON message that the Windows Syslog Agent produces and conveys to the LogZilla server. This is the data that the MS Windows appstore app receives and processes:
{
"_source_type": "WindowsAgent",
"_log_type": "eventlog",
"host": "AMBxxxxx",
"program": "Microsoft-Windows-Security-Auditing",
"event_id": "5379",
"event_log": "System",
"severity": 5,
"facility": 20,
"message": "EventID=\"5379\" EventLog=\"System\"\r\nCredential Manager credentials were read.\r\n\r\nSubject:\r\n\tSecurity ID:\t\tS-1-5-18\r\n\tAccount Name:\t\tAMBxxxx$\r\n\tAccount Domain:\t\tAARONxxxx\r\n\tLogon ID:\t\t0x3E7\r\n\tRead Operation:\t\tEnumerate Credentials\r\n\r\nThis event occurs when a user performs a read operation on stored credentials in Credential Manager.",
"SubjectUserSid": "S-1-5-18",
"SubjectUserName": "AMBxxxx$",
"SubjectDomainName": "AARONxxxx",
"SubjectLogonId": "0x3e7",
"TargetName": "WindowsLive:(cert):name=02lxtgtzzmbeitpx;serviceuri=*",
"Type": "0",
"CountOfCredentialsReturned": "0",
"ReadOperation": "%%8100",
"ReturnCode": "3221226021",
"ProcessCreationTime": "2022-04-10T02:09:44.7934892Z",
"ClientProcessId": "9744"
}
Notice that certain of these fields (such as program, event_id,
severity) are always included in the JSON event data. Other
fields (such as SubjectUserSid, TargetName, and ReadOperation)
are specific data elements associated with this type of Windows
event (corresponding to the event ID). All data fields are
available to LogZilla for handling and use.