PaloAlto
Prerequisites
The PAN-OS sources must be configured properly in order for these rules to work.
-
Configure the device to include its IP address in the header of Syslog messages, select
Panorama/Device > Setup > Management, click the Edit icon in theLogging and Reporting Settingssection, and navigate to theLog Export and Reportingtab. In theSyslog HOSTNAME Formatdrop-down selectipv4-address, then clickOK. -
Select
Server Profiles > SyslogclickAdd -
Enter a server profile
Name and Location(location refers to a virtual system if the device is enabled for virtual systems). -
In the
Serverstab, clickAddand enter a Name, IP address (Syslog Serverfield),Transport,Port(default 514 for UDP), andFacility(default LOG_USER) for the Syslog server. -
Select the
Custom Log Formattab and selectThreat, then paste the following values in the Custom Log Format area: -
Select the
Custom Log Formattab and selectThreat, then paste the following values in the Custom Log Format area: -
Select the
Custom Log Formattab and selectTraffic, then paste the following values in the Custom Log Format area:PaloAlto_Traffic type="$type" src="$src" dst="$dst" natsrc="$natsrc" natdst="$natdst" rule="$rule" srcuser="$srcuser" from="$from" to="$to" sessionid="$sessionid" sport="$sport" dport="$dport" natsport="$natsport" natdport="$natdport" proto="$proto" action="$action" bytes="$bytes" packets="$packets" dstloc="$dstloc" action_source="$action_source"Save and commit your changes.
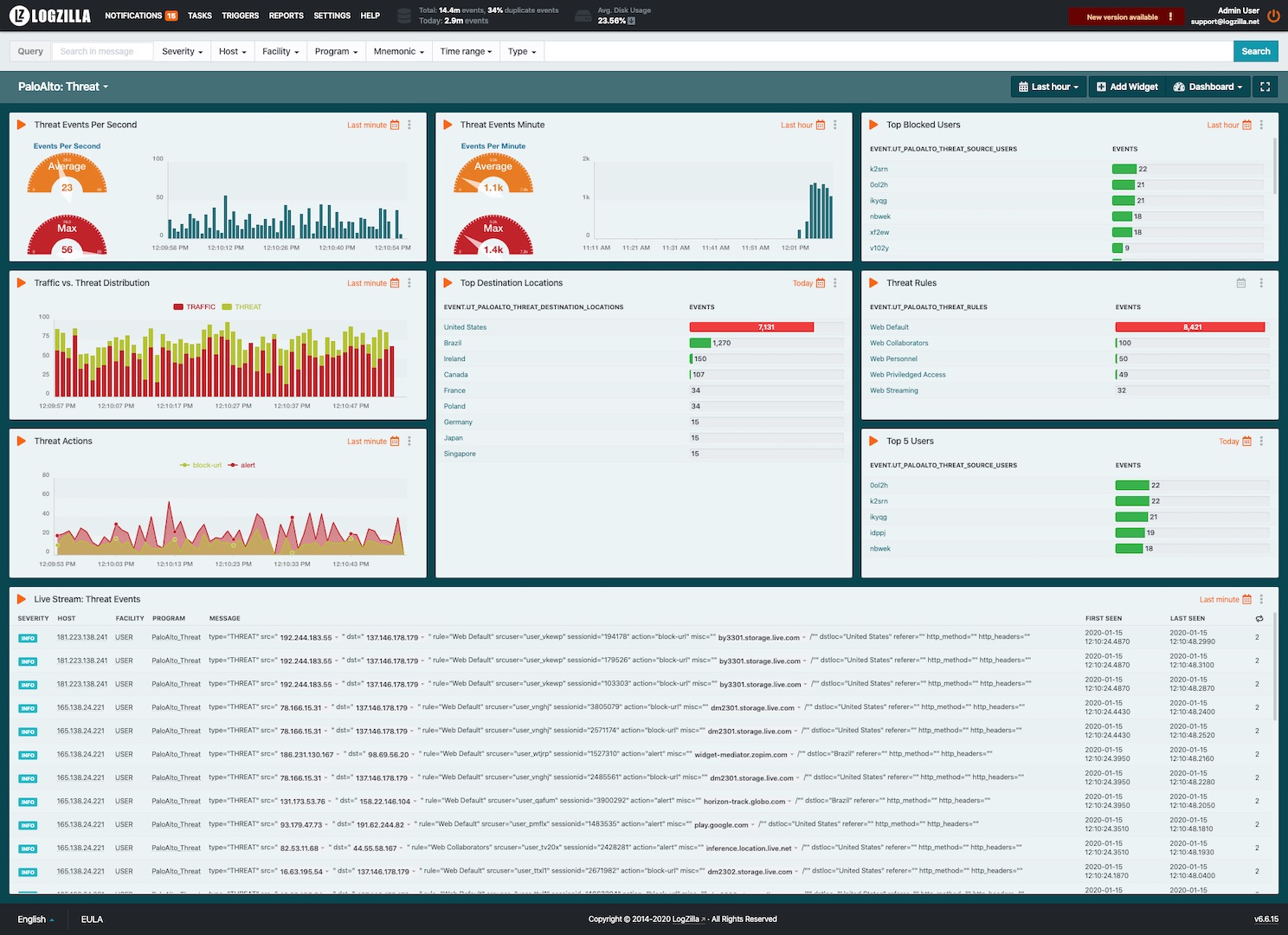
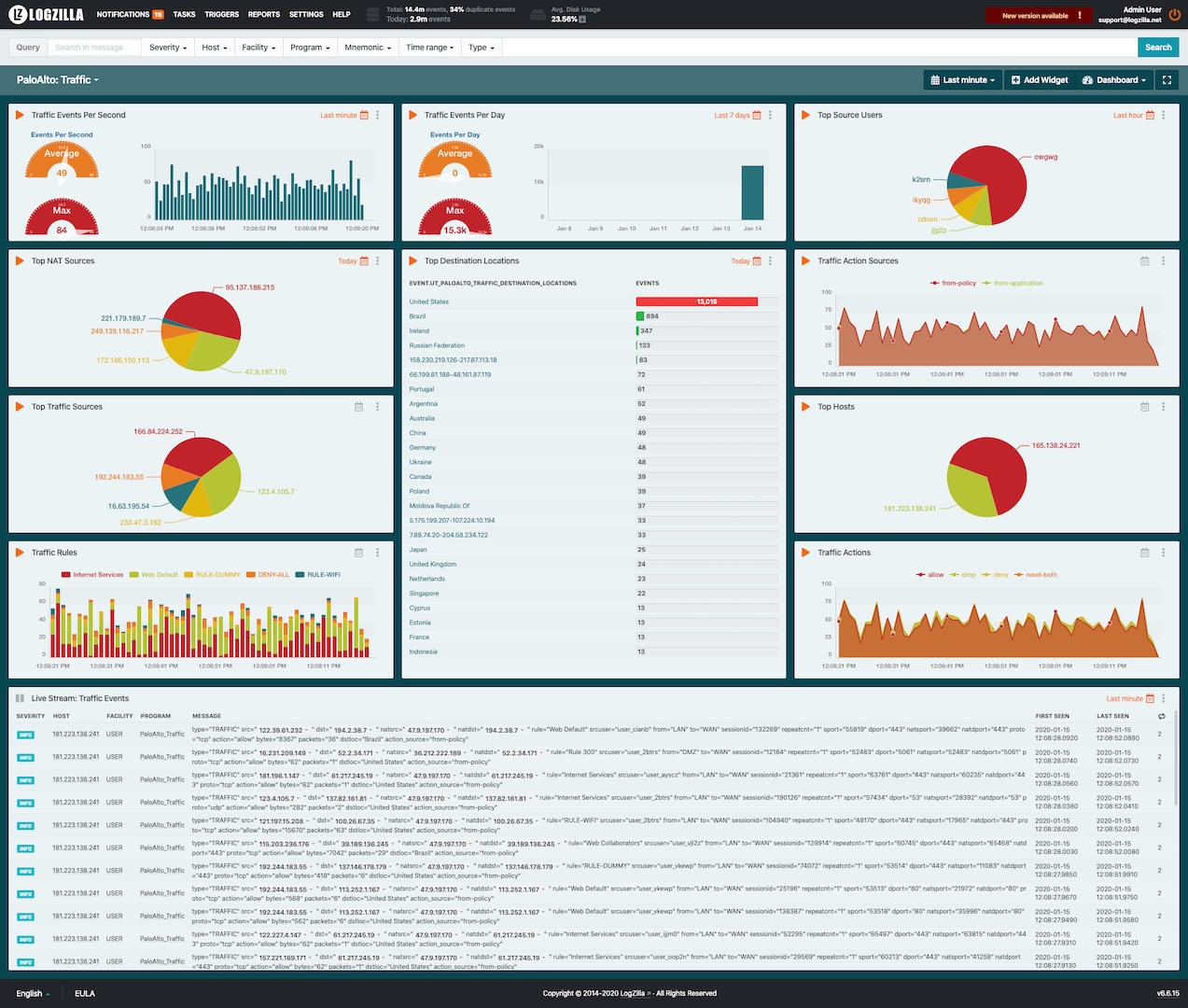
LogZilla Rules and Dashboards
We have provided rules and dashboards for PaloAlto in the LogZilla appstore. These rules and dashboards are installed by navigating to the Settings -> App store on your server.
Add the PaloAlto app to enable the rule.
After installation, your dashboards will look similar to this: